Our WideAngle global integrated security service is built on 25 years experience providing risk management services to over 8,000 customers, worldwide. We offer a combination of professional services, security solutions and managed security, powered by a security information and event management (SIEM) engine.
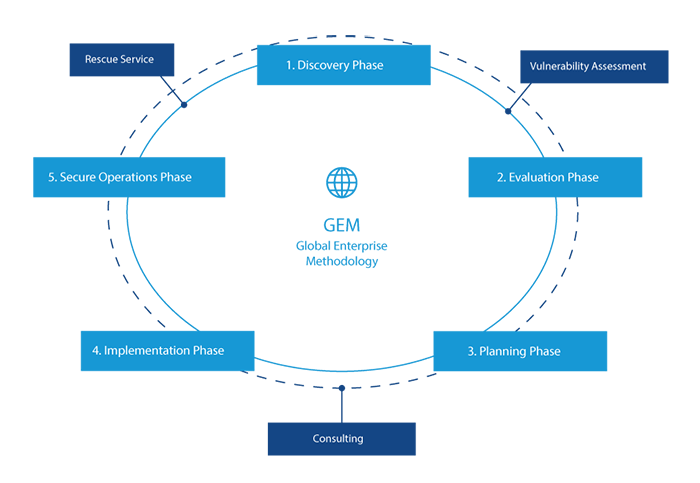
The WideAngle Global Enterprise Methodology (GEM) is based on our experience analyzing and managing global risks. GEM gives us tools to closely monitor and improve your ICT environment.
Choosing our WideAngle consulting, managed security and technology services frees you to focus on business opportunities while we focus on managing risk.
Professional Services Offered
- GEM and other consulting services, based on customer needs.
- Strategic services or advisory services by a certified expert hourly contract.
- Differing security services, varying by contract.
- Half-day security workshops based on a range of topics.
- Entry-level risk assessment.
When security incidents such as unauthorized access, malware infection or information leakages occur, our WideAngle security engineers provide an initial response, perform research and analysis, and propose improvements.
WideAngle Rescue Service provides a fixed-fee, first response pack, for emergency treatment of security incidents and the prevention of further damage. You can rely on our WideAngle Rescue Service even in situations where emergency treatment is necessary but estimated costs remain challenging.
Note: WideAngle Rescue Service only available in Japan
Our vulnerability assessment process analyzes your ICT infrastructure for weaknesses using the latest vulnerability data and knowledge. It enables us to:
- Investigate occurrences of website falsification.
- Assess unauthorized access to your ICT environment and corporate networks.
During the assessment, our engineers identify vulnerabilities to servers that store important information and propose improvement plans. The assessment ensures you always have the most accurate and up-to-date information on cyber-attacks and information leakage.
With over 900 security professionals in 14 countries, we provide unified security solutions for on-premises, cloud and hybrid ICT environments, on a global scale. Our security solutions are supported by risk analysts at our Global Risk Operation Centers (GROCs), located throughout the world.
Security Risk Identification with Big Data
GROCs conduct advanced security monitoring all day, every day. Our risk analysts uncover actual and potential security risks through automated correlation of event logs by our SIEM engine and risk analyst insight. This enables multi-layered security management of endpoints, networks, servers, applications and data, eliminating false positives and detecting previously invisible attacks. We offer:
- Intrusion prevention that can stand up to targeted attacks and other unknown threats
- Abnormal behavior detection
- Identification of infected devices
- Recovery work
- Compliance assessments
Managed Services to Match Your Budget
We offer five operational levels of security services, giving you the flexibility to select the optimal package based on your budget, current security level and risk tolerance.
Cobalt
- Device Lifecycle Management
Marine
- Risk Analysis by SIEM engine
Aqua
- Device Lifecycle Management
- Risk Analysis by SIEM engine
Night
- Risk Analysis by SIEM engine
- Additional Risk Analyst Insight with Recommendations for Improvement
Sky
- Device Lifecycle Management
- Risk Analysis by SIEM engine
- Additional Risk Analyst Insight with Recommendations for Improvement
Security Services Offered
- Network Security
Detect and block network-based threats (unauthorized traffic, intrusions, etc.) - Content Security
Detect and block network and email-related threats (malware, fraudulent emails) and inappropriate Internet access
Detect and block web application and database threats (unauthorized communications) - VM Security
Detect and block unauthorized traffic and malware (known threats) against virtual servers
- Vulnerability Assessment and Report
Uncover network, server and application vulnerabilities - Profiling
Uncover hidden threats and potential risks through analysis of network and application traffic - Real-Time Malware Detection
Detect threats hidden in websites and attachments (malware, etc.) by sandbox and detection engine - Endpoint Threat Protection
Detect, analyze, contain and eradicate threats and recover at endpoint. - Correlation Log Analysis
Improve accuracy of hidden threat detection by correlation with non-security devices (proxies, etc.)
Related Resources

White Papers
Contact our experts

 EN
EN

